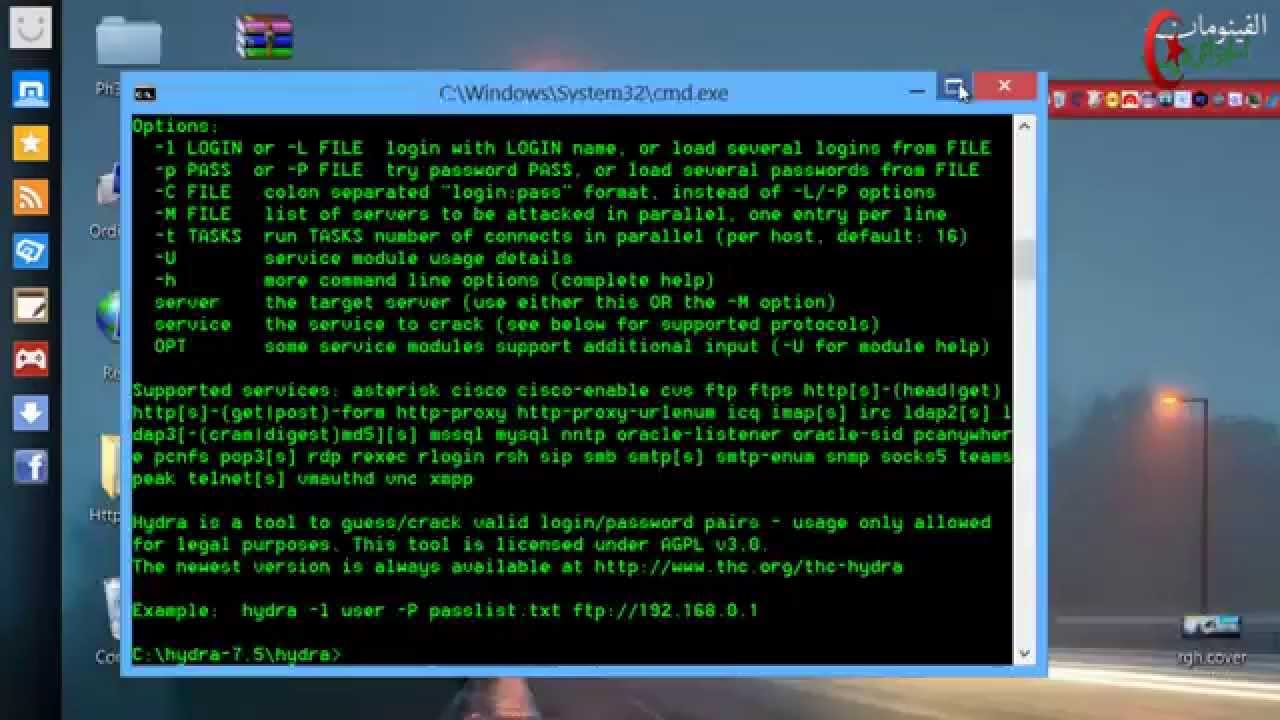
Hydra, also called THC-Hydra, is built in various Operating Systems like Kali Linux, Parrot, and other major penetration testing environments. While there are several login hacker tools that could not support more than one protocol, this tool is a command-based computer program that copies decrypt passwords from many protocols and applications with a dictionary attack. Hydra is a parallelized network logon cracker and is used only for legal purposes. Hydra could compile cleanly on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX, and macOS. This article presents you with Tutorial Install And Use THC Hydra On Kali Linux. If you are preparing to purchase your own VPS, packages of Eldernode are economical and VIP.
- THC-HYDRA 7.2 - Fast and Flexible network login Bruteforce Tool Updated One of the most famous network logon cracker – THC-HYDRA 7.2 get latest Update. Hydra is a parallized login cracker which supports numerous protocols to attack.
- THC-Hydra THC Hydra is one of the best password cracker tools and is a hugely popular password cracking software and has a very active and experienced development team. This tool is a fast and reliable network login hacking tool that uses Brute force or dictionary attacks to try various passwords.
- Sep 05, 2017 THC Hydra Download below, this software rocks, it's pretty much the most up to date and currently developed password brute forcing tool around at the moment. Number one problem with security and people getting hacked are passwords, as every password security study shows. Hydra is a parallelized login cracker which supports numerous protocols to attack. New modules are easy to add, besides that.
How To Install And Use THC Hydra On Kali Linux
Van Hauser and Ronald Kessler are the authors of Hydra. It is under the AGPL-3.0 license. As you read, Hydra is parallelized and this feature is the reason for the speed of this password cracker tool. Depend on the protocol it could be very fast. The fastest are POP3 and FTP. Researchers and security teams use Hydra to observe how they can protect themselves against the attacks. In the following, you will learn more about Hydra.
Supported Platforms
Fast Network cracker Hydra v 7.4 updated version download Junookyo's Blog. Download THC-Hydra 7.4. THC-Hydra for Windows (RARred).
-All Unix platforms such as Linux, BSD, Solaris, etc.
-macOS
-Windows with Cygwin for both IPv4, and IPv6
Mobile systems based on Linux, macOS, or QNX like Android, iPhone, Blackberry 10, Zaurus, iPaq
Supported Protocols
Unlike other hacker tools, Hydra supports multiple protocol attacks. Here is a list of them.
-Cisco enable
-Cisco auth
-FTP
-HTTP(S)-FORM-GET-POST
-HTTP-Proxy
-IMAP
-MS SQL
-MySQL
-NNTP
-IRC
-PC-NFS
-POP3
-PostgresSQL
-RDP
-SMB
-SMTP
-SNMP
-SOCKS5
-SSH
-Teamspeak
-Telnet
-VMware Auth
-VNC
-XMPP
And so on. Hydra is very fast and flexible. Also, you can add new modules easily.

Hydra Commands
Hydra is available in both command and graphical format. Type ./hydra -h to see all available command-line options or hydra for a shorter version.
_ v vrebose mode
_ l login name
_ p <password_file/wordlist>
_ e nsr, additional checks, “n” for null password, “s” try login as pass, “r” try the reverse login as pass
_ t <number of parallel connects>
_ w <max time to wait for response>
_ f: exit after first login/password pair found
_ m: OPTIONS – module specific options. See hydra -U <module> what options are available.
Install THC Hydra On Kali Linux
Hydra is pre-installed on Kali Linux and you will alreadyhave a version of Hydra installed.
But if you wish to use other Debian based Linux Operating Systems, download from the repository by running the following command:
Also, you can download the latest version from THC’s public GitHub development repository. Open your terminal and run the commands below to download, configure, compile, and install hydra:
How to use Hydra
As we mentioned, Hydra comes in two flavors, GUI-gtk and CLI version. ”hydra-wizard” is the hydra CLI guided version. So, you can use it to be guided step by step instead of typing all the commands or arguments manually into the terminal. Use the below commands from your terminal to run hydra.
1- For CLI:
2- For CLI-wizard:
3- For GUI:
Hydra-GTK
Hydra GTK is a GUI front end for hydra, as this is a GUI for hydra you do have THC-hydra already installed. While you are running Kali Linux, hydra-gtk will already be pre-installed. It is easy to be installed by running the command below:
Conclusion
Tutorial Install And Use THC Hydra On Kali Linux was presented to you with this guide. In case you are interested in reading more about the Kali Linux or Security tutorial, there are so many useful articles on the Eldernode blog. Discuss with your friends or help the beginners on Eldernode Community.
Introduction
You think your passwords are strong and secure? You are mistaken! There are numerous options to secure your password, but when it comes to the Password Cracker THC Hydra, you are done. However, you can use some of the cryptography techniques to secure your password or at least make it difficult to crack.
It’s very important to mention that this tool is just proof of concept, which gives researchers and security teams the ability to see how they can protect themselves against such attacks.
Password Cracker THC Hydra
Hydra is a parallelized password cracker which supports numerous protocols to attack. It is very fast and flexible, and new modules are easy to add. This tool makes it possible for researchers and security consultants to show how easy it would be to gain unauthorized access to a system remotely.
You will often come across information that indicates that the hydra is one of the fastest network logon crackers, also you’ll see that hydra supports multiple protocol attacks, unlike other hackers tool.
Hydra supports the following protocols:
- Asterisk, AFP, Cisco AAA, Cisco auth, Cisco enable, CVS, Firebird, FTP,
- HTTP-FORM-GET, HTTP-FORM-POST, HTTP-GET, HTTP-HEAD, HTTP-POST,
- HTTP-PROXY, HTTPS-FORM-GET, HTTPS-FORM-POST, HTTPS-GET, HTTPS-HEAD,
- HTTPS-POST, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MYSQL, NCP, NNTP,
- Oracle Listener, Oracle SID, Oracle, PC-Anywhere, PCNFS, POP3, POSTGRES, RDP,Rexec,
- Rlogin, Rsh, RTSP, SAP/R3, SIP, SMB, SMTP, SMTP Enum, SNMP v1+v2+v3,SOCKS5,
- SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
Download Telegram Download Thc Hydra Juice
Install THC Hydra
The first step is to download and compile THC-Hydra (clean compile tested on Linux, Windows/Cygwin, Solaris, FreeBSD/OpenBSD, QNX (Blackberry 10) and MacOS).
Install hydra with the following commands:

Note: For ssh module, you need to setup libssh (*not libssh2!) and for ssh v1 support, just add -DWITH_SSH1=On option in the cmake command line.
In order to install required libraries (xhydra), Ubuntu/Debian users need to run:
Exception:
- Oracle, SAP R/3 and Apple Logging Protocols modules – you’ll need to download and install them from appropriate sources;
- Other Linux derivates /BSD based systems – use the system software installer and find adequate libraries;
- Other – download & install source libraries and compile them manually.
THC Hydra Commands
- type .
/hydra -htoo see all available command line options or hydrafor a shorter version.
- –
Vvrebose mode - –
llogin name - –
P<password_file/wordlist> - –
ensr, additional checks, “n” for null password, “s” try login as pass, “r” try the reverse login as pass - –
t<number of paralel connects> - –
w<max time to wait for response> - –
f: exit after first login/password pair found - –
m: OPTIONS – module specific options. See hydra -U <module> what options are available.
Hydra Password Cracker Examples
HTTP-POST-FORM:
- http-post-form : supported service
- login_error: grep text from HTML form if login failed
- log: form username input field name
- pwd: form password input field name
FTP Example (WordList):
Download Telegram Download Thc Hydra Download
SSH Example(WordList):
Download Telegram Download Thc Hydra Oil
Telnet Example (WordList):
HTTP Login Example (WordList). For HTTPS set “https-get”:
RDP Example (WordList):
Download Telegram Download Thc Hydra Oil
MySQL Example (WordList):
Restore Aborted Session
hydra.restore file contains all necessary information for the session restore, which is written every 5 min. So, if hydra crashes or you just abort it with Control + C, you’ll find all information in that file. NOTE: you can’t copy the hydra.restore file to different platforms.
Scan/Crack Over a Proxy
The environment variable HYDRA_PROXY_HTTP defines the web proxy (*this works just for the http/www service!). Use the following syntax:
Download Thc Hydra For Windows
You can use the HYDRA_PROXY variable to scan/crack for all other services with the same syntax:
Download Telegram Download Thc Hydra Pro
Interested in Network Scanning? Check out ZMap: Fast Internet Scanner.